The convergence of artificial intelligence and cryptocurrency has created a new threat to counter-terrorism financing frameworks. By late 2025, extremist organisations such as the Islamic State-Khorasan Province (ISKP) and Hamas-affiliated fundraising networks had begun adapting their cryptocurrency fundraising to more automated, high-frequency laundering patterns. Analysts have also highlighted how autonomous AI agents can fragment large donations into micro-transactions routed across multiple blockchains, creating exactly the sort of “agentic smurfing” infrastructure these groups can exploit. This emerging method exploits critical detection vulnerabilities in current Anti-Money Laundering (AML) systems, allowing terrorist networks to circumvent traditional financial surveillance mechanisms with unprecedented efficiency. Therefore, this Insight analyses the technical mechanics underpinning agentic laundering, examines its adoption by ISKP and pro-Hamas Networks, and proposes actionable countermeasures for technology platforms and regulatory authorities.
The Operational Reality
The intersection of AI and cryptocurrency reflects the operational reality of contemporary jihadism: dispersed networks of radicalised individuals, coordinated through encrypted platforms, driven by Salafi-jihadist ideology that frames financial support as a religious obligation. ISKP’s external operations targeting Russia, Iran, Turkey, and Western Europe throughout 2024-2025 demonstrated the group’s expanding transnational reach and its urgent need for financing mechanisms that could survive aggressive law enforcement interdiction. The March 2024 Moscow Crocus City Hall attack, which killed over 140 people, had been partially financed with approximately $2,000 in cryptocurrency, funds that investigators traced only after the attack had occurred.
ISKP’s Central Asian recruitment networks exploit kinship ties and sectarian grievances to radicalise Tajik and Uzbek migrants. Hamas leverages resistance narratives and diaspora support to sustain fundraising, despite intensive enforcement. Both groups require steady financial flows to cover day-to-day operational costs, such as safe houses, encrypted communications, travel documents, and stipends. Traditional threshold-based AML systems, designed to detect large transfers, systematically fail when terrorists fragment those same funds into micro-amounts that blend seamlessly with legitimate decentralised finance (DeFi) activity.
Meanwhile, Hamas-affiliated networks continued soliciting donations despite announcing in April 2023 that they had ceased cryptocurrency fundraising. By March 2025, the U.S. Department of Justice seized approximately $200,000 in USDT following a forensic analysis that identified 17 cryptocurrency addresses shared via encrypted group chats, with operational wallets receiving approximately $1.5 million since October 2024. This pattern of public disavowal, followed by covert continuation, reflects a broader shift in terrorist operational security.
From Mixers to Machines: The Tactical Evolution
Traditional terrorist financing relied on cryptocurrency mixers like Tornado Cash – a decentralised protocol that anonymises transactions – to obscure fund trails by pooling and redistributing transactions. However, following the December 2025 takedown of remaining major crypto mixing platforms, some terrorist organisations pivoted towards automation. This shift represented a calculated response to enforcement pressure, leveraging the same autonomous AI agent infrastructure that legitimate crypto traders were deploying for high-frequency DeFi strategies.
The technical process of agentic smurfing operates in four distinct phases. First, AI agents programmatically generate disposable wallet addresses using autonomous wallet software development kits (SDKs) that create unique addresses without centralised control. These “burner wallets” are used for single transactions before being abandoned, leaving minimal forensic fingerprints. Unlike static wallet addresses, which enabled authorities to freeze ISKP assets following the Moscow attack, disposable addresses defeat address-based blacklisting.
Second, machine learning algorithms analyse blockchain congestion patterns and transaction fee structures to optimise timing and routing. This is a strategic deployment of AI to ensure micro-transactions blend within legitimate network activity. ISKP-affiliated transfers frequently occurred during peak trading hours on TRON, a blockchain network widely used for stablecoin transactions, capitalising on its sub-cent gas charges and throughput of more than 2,000 transactions per second.
Third, funds are fragmented into micro-amounts and deliberately calculated to remain below regulatory thresholds. The FATF Travel Rule mandates transaction monitoring for transactions above $1,000, whilst FinCEN Currency Transaction Reports focus on thresholds of $10,000. By operating in this regulatory blind spot, typically fragmenting donations into $50 – $500 transfers, terrorist financiers exploit the reality that compliance systems lack sufficient resolution to detect distributed micro-transaction patterns. A $100,000 donation can be fragmented into 2,000 separate $50 transfers, spread across multiple days and wallets, mimicking ordinary user activity.
Finally, cross-chain atomic swaps enable instantaneous cryptocurrency exchanges across multiple blockchains without intermediaries. Unlike traditional exchanges that maintain comprehensive transaction logs and comply with Know Your Customer (KYC) protocols – identity verification and customer-due-diligence requirements designed to link transactions to real users -, atomic swaps occur peer-to-peer through decentralised bridge protocols, leaving only minimal on-chain evidence. Elliptic documented over $21.8 billion in laundered funds through cross-chain methods in 2025, a fivefold increase from 2022.
ISKP and Hamas: Ideologically-Driven Technical Adaptation
ISKP’s monthly cryptocurrency revenues, estimated between $25,000 and $100,000, proved sufficient to fund multiple high-impact external operations whilst remaining below thresholds that trigger intensive investigation. Over the past year, TRM identified hundreds of transactions linked to ISKP, ranging from $100 to $15,000. These transactions have flowed through regulated exchanges and individual cryptocurrency traders. Technical analysis reveals ISKP exploited TRON’s TRC20 standard for USDT transfers. In 2025, TRON accounted for approximately 58% of identified illicit crypto volume across the major blockchains, with stablecoins responsible for about 63% of laundering activity overall.
ISKP’s propaganda system plays a critical enabling role. Following the Moscow attack, ISKP released AI-generated propaganda bulletins featuring deepfake-enhanced images and synthetic voices. These channels increasingly share cryptocurrency best practices, including tips on using unhosted wallets, mixers, and fake credentials to bypass KYC controls. The recruitment strategy amplifies its financing capabilities. The group exploits kinship networks amongst Central Asian migrants in Russia and Turkey, leveraging pre-existing bonds of trust and family obligation to radicalise new supporters. When fundraising and recruitment operate through the same kinship networks, donor identification is extraordinarily difficult.

Figure 1. A screenshot of ISKP’s newsletter requesting cryptocurrency contributions, illustrating the group’s use of decentralised finance to move funds anonymously.
Hamas-affiliated fundraising networks operate within a different ideological framework but demonstrate parallel technical adaptation. The Gaza-based organisation GazaNow received nearly $4.5 million in crypto donations following the 7 October 2023 attack, resulting in U.S. and UK sanctions and blacklisting by Tether. Despite these enforcement actions, TRM data indicated the group still received tens of thousands of dollars in cryptocurrency donations, albeit more discreetly. Several other fundraising initiatives have collected tens of thousands of dollars, notably one backing the Mujahideen Brigades, the militant branch of the Palestinian Mujahideen Movement, which the United States placed under sanctions in November 2018.
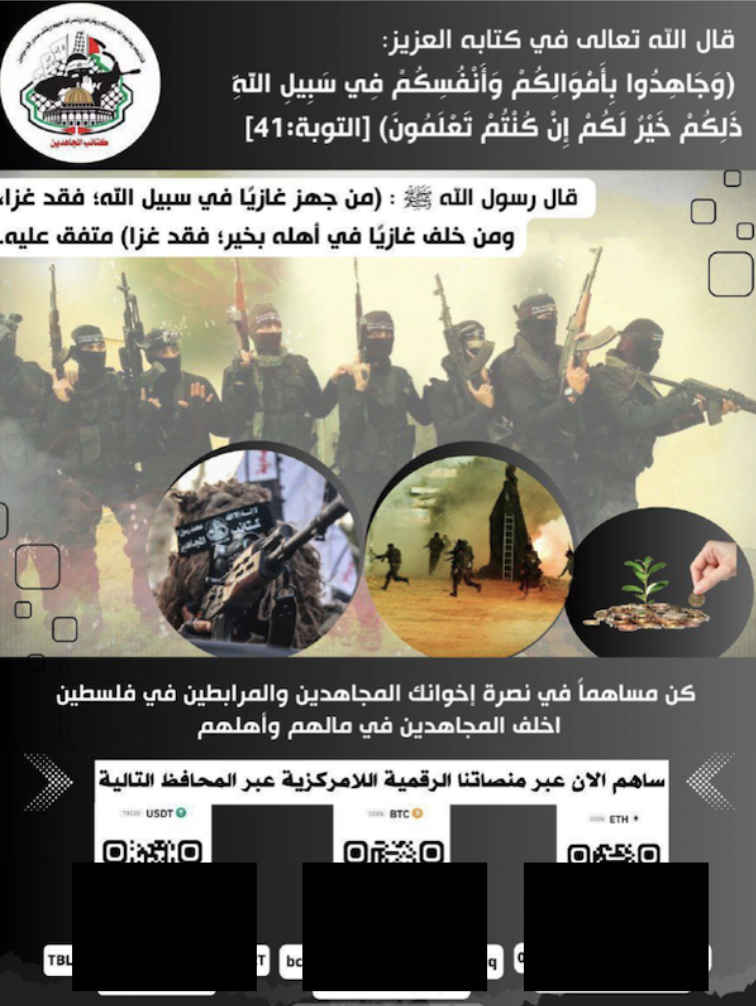
Figure 2. A Mujahideen Brigades fundraising campaign seeking cryptocurrency donations, showing how militant groups leverage digital currencies to bypass traditional financial oversight.
In response to intensified asset seizures, Hamas-affiliated networks adopted high-frequency “bridge-hopping” across multiple blockchains. This technique leverages cross-chain bridge protocols to rapidly transfer funds between Ethereum, TRON, Binance Smart Chain, and others, creating transaction complexity that overwhelms traditional forensic tools. The advantage comes from delays in tracking, as it takes time to trace transactions on the blockchain. During that period, terrorists collect the funds and convert them to cash through unlicensed over-the-counter (OTC) brokers.
The Detection Gap: Why Counter-Terrorism Finance Systems are Failing
Current counter-terrorism finance systems are structurally misaligned with how terrorists use crypto today. Regulatory frameworks still rely on value thresholds: the FATF Travel Rule requires full sender/recipient information only above ~USD/EUR 1,000, while the EU’s MiCA sets thresholds for obliged entities. U.S. Treasury’s 2024 DeFi Risk Assessment warns non-compliant DeFi is a major money-laundering/terror-finance gap, as decentralised protocols handle rising illicit flows. These assume serious threats involve large sums, yet case studies show attacks like Manchester Arena 2017 (explosives < £100) or London Bridge (kitchen knives) cost little, enabling terrorists to split five-figure donations into thousands of sub-threshold crypto transfers that slip past monitoring.
Cross-chain chain-hopping further erodes attribution. Elliptic’s 2025 report estimates that criminals have moved more than 21 billion USD through decentralised exchanges, cross-chain bridges, and swap services, and stresses that rapid chain-hopping across multiple blockchains makes tracing extremely difficult without integrated, multi-chain analytics. During the weeks or months to reconstruct flows, funds consolidate and cash out via small exchanges and unlicensed OTC brokers, a pattern seen in U.S. actions against Hamas-linked services like BuyCash.
Finally, behavioural detection struggles in an environment where both legitimate and illicit users generate dense patterns of small transactions. Normal DeFi usage now includes high‑frequency micro‑activity from staking, automated yield strategies, NFT trading and algorithmic execution, producing transaction streams that look, at an abstract level, very similar to automated laundering patterns. Against that backdrop, the overall volume of suspect flows is exploding: early reporting on Chainalysis’ 2026 crypto crime data indicates that addresses linked to illicit activity received at least 154 billion USD in 2025, a 162% increase over the revised 2024 figure, driven largely by sanctioned entities and state‑linked actors.
Actionable Solutions: Integrating Counter-Terrorism Intelligence with Financial Disruption
Addressing agentic smurfing in a terrorist‑financing context requires coordinated interventions that move beyond threshold-based detection towards pattern recognition, cross‑chain coordination and the integration of financial intelligence with broader counter-terrorism objectives.
AI‑driven micro‑transaction clustering is the first pillar. Traditional address clustering relies on common‑input ownership assumptions, but – as previously stated – agentic smurfing by groups such as ISKP and Hamas‑linked fundraising networks deliberately avoids these patterns.
Next‑generation approaches, therefore, need to focus on behavioural pattern recognition that identifies “micro‑transaction storms” – statistically anomalous spikes in sub‑threshold transfers with coordinated timing, counterparties, and routing across chains, enabling investigators to isolate terrorist micro‑laundering flows from benign DeFi noise. Recent blockchain analytics research shows that combining clustering and anomaly‑detection methods (such as K‑means with supervised models like logistic regression or tree‑based classifiers) can reliably flag suspicious transaction clusters when trained on rich labelled data, enabling detection of automated, attack‑linked funding patterns rather than only large single transfers. In parallel, smart‑contract-level clustering and bytecode similarity analysis can reveal families of addresses created and controlled by the same automated system, even when individual wallets are short‑lived, helping investigators unmask the infrastructure behind AI‑generated disposable wallets used in terrorist agentic smurfing. For technology platforms and financial intelligence units, this implies deploying always‑on, AI‑driven clustering engines integrated with operational intelligence – more akin to signals intelligence collection than traditional case‑by‑case AML – so that automated alerts on emerging micro‑transaction patterns feeding extremist networks can be triaged rapidly by human analysts.
The second pillar is real‑time multi‑chain AML coordination tailored to terrorist threats. Current counter‑terrorist financing arrangements are fragmented across jurisdictions, asset classes and service providers, while cross‑chain money laundering has scaled rapidly. To respond at the necessary speed, regulators and platforms need joint intelligence‑sharing frameworks that link stablecoin issuers, major exchanges, blockchain analytics firms, law enforcement and financial intelligence units in near real time, so that wallets associated with ISKP, Hamas and similar actors can be identified and frozen before funds reach operational networks. One model is the T3 Financial Crime Unit (T3 FCU) – a public‑private partnership launched in 2024 by TRON, Tether and TRM Labs. It reports having frozen more than 300 million USD in illicit proceeds by late 2025 through coordinated identification and blocking of suspect wallets, including wallets linked to sanctions‑evasion and terror‑adjacent activity. Expanding this kind of rapid‑response freezing protocol across other major stablecoin issuers and exchanges would allow blockchain‑level analytics to feed directly into operational disruption, so that insights from on‑chain patterns are fused with signals, human and open‑source intelligence about extremist networks, rather than being kept in compliance teams.
The third pillar is sandboxed AI analysis and verification frameworks, designed with terrorist exploitation in mind. As autonomous agents increasingly manage wallets, execute trading strategies and route payments, they dramatically expand the attack surface, but they also offer an opportunity: the same infrastructure can be instrumented to generate detailed telemetry on transaction timing, volume and routing that feeds anomaly‑detection systems tuned to spot coordinated laundering operations and covert funding streams. For environments at risk of terrorist abuse, secure execution should incorporate strong intent‑verification layers – for example, combining decentralised identifiers (DIDs) and verifiable credentials with on‑chain proofs of intent and zero‑knowledge techniques – to ensure that each agent‑initiated transfer is cryptographically tied to an authorised policy and cannot be silently repurposed for laundering or operational preparation. Within such sandboxes, platforms can apply continuous behavioural profiling to autonomous agents, learning normal patterns for specific strategies and rapidly flagging deviations associated with smurfing or chain‑hopping, while updating detection models as adversaries adapt their evasion techniques, thereby turning AI from a force multiplier for agentic smurfing into a critical tool for early detection and disruption of terrorist financing.
—
Daria Alexe is a Master of Science student in Intelligence and Security Studies at Liverpool John Moores University. She has previously worked as a geopolitical analyst and holds a Double Bachelor of Arts in Global Governance and Political Science, as well as a Master of Arts in Prevention of Armed Conflicts and Terrorism. Her work focuses on international security, terrorism, and CBRN threats, conducting intelligence and geopolitical analysis on extremist networks and illicit activities in high-risk contexts.
—
Are you a tech company interested in strengthening your capacity to counter terrorist and violent extremist activity online? Apply for GIFCT membership to join over 30 other tech platforms working together to prevent terrorists and violent extremists from exploiting online platforms by leveraging technology, expertise, and cross-sector partnerships.
