There has been considerable concern about the threat of online radicalisation from policymakers, the media, and academics. This is unsurprising given the vast proliferation of communications technologies in recent decades, which has coalesced with notable terror threats from both jihadist groups such as the so-called Islamic State (IS) and a resurgent far-right. Existing research has shown that terrorists do utilise the Internet heavily as part of their pathways, however, it does not appear to be replacing the offline domain (although there are some exceptions). Face-to-face interactions, local networks, and existing predispositions still seem to be key. In fact, ‘online’ and ‘offline’ extremist behaviours often blur in ways that make it difficult to establish in which domain the activity is taking place. In an Insight for the Global Network on Extremism and Technology in 2020, we drew from a range of cases to demonstrate that terrorists’ activities split across both domains and argue that there may be a systematic bias in reporting of terrorism cases that prompt audiences to believe the Internet plays a greater role than actually pertains.
Recently, we published an article in Terrorism and Political Violence which aims to expand upon this research by conducting a cluster analysis on 231 IS terrorists in the US, assessing whether their online and offline behaviours formed discernible pathways. We coded for 18 ‘network’ variables such as engaging in a virtual network and attempting to recruit others offline and 16 ‘event’ variables such as conducting preparatory acts online and engaging in physical training. This is an exploratory approach which has been used by terrorism scholars previously to establish the patterns of behaviour of lone actor terrorists as well as comparing them to mass murderers. Our aim is to provide a degree of nuance to debates around online radicalisation by creating ‘ideal type’ pathways which help to explain the ways in which terrorists behaviours interact in both domains. Rather than a simple dichotomy – ‘online’ vs ‘offline’ radicalisation, our analysis yielded four pathways that sit on a spectrum of Internet usage.
The ‘Integrated’ Pathway
Individuals in this pathway had heavy engagement with co-ideologues across both domains. Moreover, they also used both domains for their event planning activities. A sizable portion of terrorists in this pathway executed their plots as part of a wider group, but also maintained online contact with co-ideologues beyond their cells. A good example of this is David Wright, who plotted with Nicholas Rovinski and Ussamah Rahim to murder right-wing blogger Pamela Geller in 2015. These three interacted online and offline with each other, but Wright also maintained online communications with British hacker Junaid Hussain, who was assassinated via drone strike in 2015 and Zulfi Hoxha, an alleged foreign fighter from the US who later became a prominent member of IS. Wright was part of the wider radical online milieu throughout their radicalisation trajectories and used social media to maintain contact with close peers with whom they had pre-existing relationships but also with like-minded individuals much further afield.
The ‘Encouraged’ Pathway
Actors in this trajectory tended to use the Internet heavily for both networking and event-planning behaviours. Unlike the ‘Integrated’ pathway, there is considerably less offline contact within this group. As a result, actors tended to use the Internet for preparatory behaviours, possibly because of the affordances the Internet offers which can supplement the lack of face-to-face communications. Despite most of the behaviours in this group being online activities, it should not necessarily be seen as online-only radicalisation – as we discussed in our previous Insight, this sample had only five potential cases of this, and even those could not be confirmed. This pathway shows that there is a wider pool of individuals with little, but some, offline activity. The above-mentioned Zulfi Hoxha, who allegedly travelled to Syria in 2015, maintained contact with co-ideologues via platforms such as PalTalk and Skype, while using this connection to disseminate issues of Dabiq – IS’ official magazine. Hoxha also received both logistical and financial support online; Wright and Rahim helped him plan his trip and helped raise money for him by selling the latter’s laptop on Craigslist.
The ‘Isolated’ Pathway
Unlike the previous two trajectories, the clearest defining feature of this pathway is a lack of integration with co-ideologues in either the online or offline domain. This does not mean there is no communication at all and individuals are ‘true’ lone actors with no wider connections – this is incredibly rare. Rather, simply that there are less clear network connections in either domain. Actors within this pathway differed in terms of how they used the Internet to learn about their event. Bernard Augustine, who attempted to join IS in Libya, used the Internet to purchase plane tickets; watch propaganda videos; as well as using search engines for advice on how to travel. While it remains possible that the court filings omitted discussions with co-ideologues, the information in the public domain suggests that he had little-to-no contact with any facilitators. Others had little in the way of a digital footprint; Mahad Abdiaziz Abdiraham attacked two individuals with a knife at a Mall of America in Minnesota, claiming he was called upon by the now-deceased IS leader, Abu-Bakr al Baghdadi. He had no known connections to a wider network and did not seem to use the Internet to plan either, instead seemingly acting on the spur of the moment.
The ‘Enclosed’ Pathway
In the final ideal-type trajectory, individuals had substantially greater offline network interactions than online – in contrast to the ‘Encouraged’ pathway. However, this is not to say that individuals did not use the Internet at all. An illustrative example is the cluster of travellers (successful and unsuccessful) from the Minneapolis/St Paul area. This was tight-knit group of friends and family who regularly met face-to-face to socialise and plan their travel. However, these individuals still used the Internet to plan their plots as well as accessing and sharing propaganda with each other. Moreover, after some members of the group – like Abdi Nur – travelled, they kept in contact via social media with those at home, encouraging them with stories about life in the caliphate. Even in the pathway that is most identified by strong offline connections, the Internet still protrudes in a meaningful manner. This lends further weight to the argument that ontologising an online space that is distinct and autonomous from the offline domain may be a false dichotomy.
It’s now 13 years ago that Marc Sageman declared that “face-to-face radicalization has been replaced by online radicalization.” Not only do our findings add to the weight of literature which demonstrates that this is not the case, but our four empirically derived pathways challenge the notion that radicalisation can be easily demarcated into ‘online’ and ‘offline’. Behaviours spill over both domains in complex and multifaceted ways. Identifying pathways which account for this is the first step in moving beyond this simplistic dichotomy.
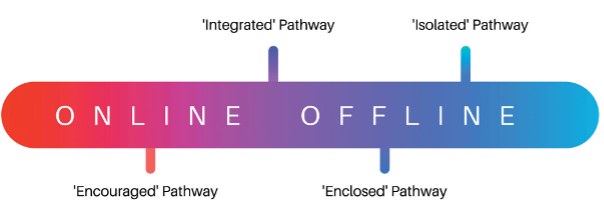
Given that there are so few individuals that could be described as radicalising entirely online or offline, understanding these pathways on a spectrum may be more fruitful way of understanding the role of communications technologies in terrorism. Here we can see, neither end of the spectrum can be described as fully ‘online’ or ‘offline’. Terrorists largely operate, to at least some degree, in both domains.
