With the multiplication of online jihadi content and terrorist attacks in the West in recent years, some users and hacktivist groups, such as Anonymous, have taken on the moral duty and assumed responsibility for denouncing terrorist accounts to companies. This kind of citizen-led surveillance extends the sets of policing tactics which take place on social media platforms, and impact both the nature of visibility and interaction between users. It is currently unclear exactly when Anonymous and other hacktivists first began their mobilisation efforts. However, in the wake of the 2015 attacks on Charlie Hebdo’s offices, Anonymous affirmed its willingness to fight back against Islamist websites, as well as social media accounts, that belonged to suspected extremists. Since then, several operations such as #OpCharlie, #OpIsis, or #OpDaesh – to name a few – have been launched on Twitter. Subsequently, other groups began to emerge, such as Ghost Security Group, Controlling Section (CtrlSec) and the Katiba des Narvalos; all formed with the specific intention of combatting online jihadi propaganda.

Screenshot of Controlling Section’s Twitter page
In addition to the aforementioned claimed groups, many anonymous users are also involved in this struggle. These hacktivists generally refer to themselves as “jihadi hunters”. Their intended goal is clear: to destroy Islamic State’s (IS) online presence by flagging their accounts to Twitter. To that end, they list and flag jihadi accounts found on the platform and then ask users to report the accounts in order to generate massive reporting numbers. These cyber-vigilantes might also partake in humorous counter-propaganda work by producing parodies or mockeries of jihadi content.
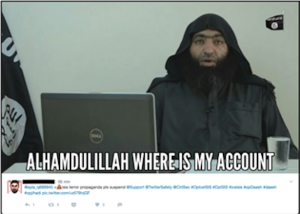
Screenshot of a tweet published by a cyber-vigilante
While anti-jihadi groups petition Twitter to delete jihadist accounts as well, there is no indication as to whether Twitter acts upon the information they provide nor whether they delete accounts affiliated with the terrorist organisations. The company appears to rely solely on reports from individual Twitter users and the authorities. It is therefore difficult to know precisely how these lists are actually used, and how many Twitter users end up reporting suspicious accounts in response to an appeal from a cyber-vigilante group. As J.M. Berger and J. Morgan point out, the actions undertaken by these groups may indeed have an effect, but it remains impossible to measure.
Islamic State’s Response
Faced with daily reports from jihadi “trackers”, IS militants have adopted a new strategic position to stem these threats. In addition to the fact that denunciations can give rise to heated altercations between the two communities, much like the anti-jihadists, IS will go ahead and report their opponent’s accounts. As such, IS militants make false reports on anti-jihadist accounts through accounts managed by humans or botnets. To deploy their reporting arsenal, the collective uses a range of methods to avoid looking like Islamic State supporters. For instance, they adopt a “neutral” account or create a series of fake accounts where they hijack the anti-jihadist’s passwords and usernames to carry out mass-reporting attacks. These mass-reporting attacks are often led by human or suspicious accounts.
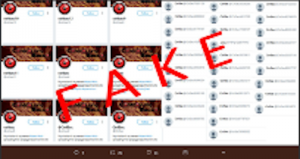
Screenshot of IS militant attack on Controlling Section
When Twitter removes reported accounts, it shows that the platform is extremely poor at differentiating nuances and context. In other words, platforms such as Twitter do not assess the nature of whistleblowers. The algorithm’s sole concern is the number of mass reports submitted. However, it is difficult to establish whether account suspension errors occur as a result of negligence, faulty algorithms or mistakes committed by moderation teams. Platforms are generally not forthcoming about their failings.
Thus, cyber-vigilantes always submit the same complaints: hundreds of users invested in the anti-jihadi fight find themselves harassed, attacked, blocked, and suspended by accounts held by extremists that continue to prosper. Platforms thus contribute to establishing power struggles and lateral surveillance between different communities who fight each other using monitoring and hostile reporting methods. The one who comes out on top is the one who manages to silence the other party. Still, neither of the two communities has yet been fully silenced. One consequence is rather the extent to which visibility activity on social media is destabilised and momentarily interrupted.
