Introduction
The Islamic State (IS) has evolved to be one of the most serious threats to many states, no matter the state’s status of power. The Islamic State has firmly established a presence in the Sahel Region, advancing its goals of radicalisation and the eventual establishment of a Caliphate. Ongoing socio-political instability in the region has created an environment where the group can easily exploit vulnerabilities and recruit individuals. However, how the Islamic State has radicalised individuals from highly secure and stable political societies remains more fraught. This raises a crucial question about how technology enables terrorist outfits to advance their propaganda machinery making radicalisation rapid and more pervasive, highlighting the need for a multifaceted approach to counter this threat effectively.
This Insight will qualitatively assess the organisational influence, network reach and operational capacity of The Islamic State Khorasan Province (ISKP) using Social Network Analysis (SNA) in the context of technology-driven terrorism. A comparative assessment of ISKP and other regional terror outfits will provide an outlook for mapping the interconnectedness of alliances and rivalries. SNA highlights key nodes (individuals or platforms) and edges (connections), offering insights into these networks’ strengths, adaptability, and vulnerabilities. This Insight will also highlight the impact these nodes and edges have on the Taliban interim government; and the political relationship dynamics between Pakistan and Afghanistan that shape the regional geopolitics.
Social Network Analysis and Terrorist Networks
In 2019, following the elimination of Abu Bakr al-Baghdadi in a US special operation, ISKP had no option but to shift its Territorial Control (Tamkeen) strategy to the Terrorist Networking Phase because an obliterated IS leadership weakened its capacity. It adapted to strategies like Urban bombings and radicalisation, leading to lone-wolf attacks.
It becomes important at this juncture to analyse the radical networks that exist and are active predominantly in South Asia. ISKP, one of the most active affiliates of the Islamic State core, uses its multilingual strategy of disseminating propaganda that reaches a wide variety of regions. The idea to recruit those of Tajik origin to orchestrate the Crocus City Hall Attack in Moscow and of Indian origin to attack a Gurudwara in Kabul connect these dots; it is geographical expansion not through power consolidation but through cyberspace.
Social Network Analysis (SNA) is one theory that aims to understand how relationships and communications work in a structured network. To employ SNA in terrorism studies, the analyses’ gaps and limitations must be identified. Subsequently, when it comes to the network of terrorist organisations, clear data about the leadership and hierarchy is unclear to open research. For OSINT researchers, this demonstrates SNA’s limitations. However, SNA is still considered a potential method for effective and efficient counter-terrorism measures. SNA’s continued development in this context has enhanced its ability to analyse targeted networks, identifying both their strengths and vulnerabilities.
Through SNA, it was possible to establish the relationship dynamics between the Islamic State (ISIS, ISKP, ISPP, ISHP) and other major regional terror networks, including Al-Qaeda, Haqqani Network, Tehrik-e-Taliban Pakistan (TTP), Lashkar-e-Taiba.
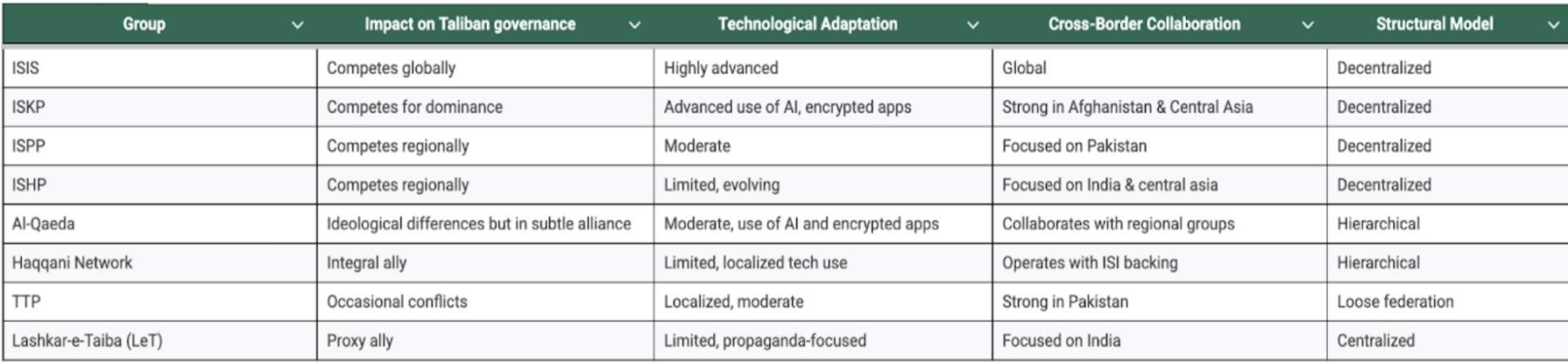
Figure 1: SNA simplified into a tabular format to infer the relationship dynamics and the technological adaptations.
To better understand the relationship dynamics and analyse the impact, the groups have been divided into three: Terror Network A, Terror Network B, and States.
Terror Network A: Islamic State – ISIS (leadership) , ISKP, ISPP, ISHP (Central Asia & South Asia)
Terror Network B: al-Qaeda, Haqqani Network, TTP, Lashkar-e-Taiba
States: Afghanistan (Taliban), Pakistan
Group A possesses advanced cyber capacity, a multilingual strategy, professionals from IT hubs working for their propaganda curation and dissemination, active social media campaigns, and is not solely focused on localised issues. Moreover, decentralisation through technology has helped the group intangibly expand to shape regional geopolitics.
Group B mostly focuses on regional agendas but is aligned through political pursuits. Groups like TTP, and Lashkar-e-Taiba focus on a localised agenda. Haqqani Network is an integral part of the Taliban Cabinet, and therefore it stays under the shadow. Al-Qaeda is the only strongest rival to Group B components, but its activities have been limited due to its alliance with the Taliban. Concurrently, the Taliban has been long-pressured by the international community to limit the activities of al-Qaeda. Yet, al-Qaeda is also strategising to decentralise, adopting techniques used by IS due to the availability of technology at their disposal. Al-Qaeda, TTP and Haqqani Network are in alliance with the Taliban interim government, where the state power boosts its activities but with limitations due to the international monitoring in Afghanistan.
As for the case of states, Taliban’s cabinet minister Khalil ur-Rahman Haqqani was assassinated at a crucial timeline when Afghanistan and Pakistan were slowly moving towards better relations, mainly through the progress on the issue regarding the Tehrik-e-Taliban Pakistan (TTP) group. An additional highlight is that the Haqqani Network is supported by the Inter-Services Intelligence (ISI) of Pakistan. In an attempt to ease tensions and stop the TTP’s increasing attacks in Pakistan, senior Pakistani officials met with the Taliban representatives in Islamabad. These tense Afghanistan-Pakistan relationships might be stabilised by these dialogues, which were viewed as icebreakers. However, with rising scepticism and volatility in the bilateral relationship, Haqqani’s death threatens this delicate development, which the ISKP had hoped for. The TTP’s ongoing attacks in Pakistan, despite the Taliban’s guarantees, erode its credibility, adding to the strain already placed on the Taliban.
The Islamic State Network (ISIS, ISKP, ISPP, ISHP) have advanced technological adaptations, including artificial intelligence and media tools like deepfakes to manipulate narratives. Al-Qaeda stands secondary in terms of technological abilities. However, al-Qaeda’s revival and expansion into India and Africa have to be monitored well. The most threatening group today, undoubtedly, is the Islamic State. Nevertheless, al-Qaeda’s consistent anti-west agenda poses a great danger to Western nations.
In the overall jihadist network present in the region, ISKP stands isolated, having no alliances with any other groups except Lashkar-e-Jahngvi in Balochistan (Pakistan). The Taliban interim government has been fighting the ISKP and managed to arrest several members of the group. However, ISKP has only managed to increase its number of recruits. Mass recruitment has been taking place, and technology has given the biggest advantage to these terror networks in order to decentralise and reach individuals with ease, thanks to encrypted networks.
It is to be noted that the Taliban interim government faces three most important challenges: ISKP, Straining relations with Pakistan, and the absence of a Taliban representative at the United Nations. Taliban’s efforts to build diplomatic ties with nations that ISKP views as despots who oppose Islam accelerates ISKP’s objective of toppling the Taliban regime.
New Developments Within the IS Network
ISKP’s online propaganda tool, “Voice of Khurasan”, has been instrumental in spreading its message in the English language globally. ISKP has also recently revived its official radio station, “al-Bayan”, which broadcasts conversations between the groups and potential recruits or radicalised individuals who have already pledged allegiance to the Islamic State. The Islamic State’s current strategy is centred on the consolidation of its network through decentralisation. Among the drivers of this is the widespread adoption of modern technology, including artificial intelligence and algorithm-driven jihad in chatbots. By dispersing leadership and leveraging these tools, the outfit has enhanced its ability to adapt swiftly to evolving circumstances, ensuring its global jihadist momentum is continued.

Figures 2 & 3: Screenshots from the “Voice of Khurasan,” where the translated transcripts of the radio broadcasting are published with questions and answers.
Social Network Analysts question whether terrorist recruiters are generally connected to the organisation through weak ties – informal/acquaintance-like connection – or strong ties – close, trusted relationships—as this connection influences the activities of the recruited individuals within the network. Determining this distinction can potentially assist intelligence agencies to curate strategies for effective counter-measures.
ISKP is the primary concern in the Central Asian region, particularly Afghanistan and several other nations as well, including the U.S. and Russia. The Islamic State gains a strategic edge by recruiting disillusioned members of various terror networks or even government agencies, turning its knowledge of rivals’ strengths, vulnerabilities and intel into a deadly weapon. Global intelligence agencies and government authorities must concentrate on this particular core because, if the ISKP is not addressed and countered, it will fuel instability and geopolitical tensions that affect not only the region but the global sphere.
Conclusion and Recommendations
Today, the fight against terrorism takes place in the boundless realm of the internet, where networks and narratives are the preferred weapons, transcending national boundaries, battlefields, and gunfire. If the ISKP is to be dismantled, government agencies must adopt not only innovative strategies on land but also in the virtual space, where encrypted messages and propaganda spread like wildfire. The responsibility no longer lies solely with governments; tech companies must step up, developing predictive algorithms, monitoring user activity, and deploying AI-driven countermeasures to fight back against these shadowy networks.
Social Network Analysis has to be employed by social media and consumer interactive tech companies to trace out all the loopholes of communication and channels within specific terror networks. Through SNA, the technological adaptability being identified gives companies an ample amount of potential information to advance their programming and secure it constructively. Content analyses of certain terror propaganda materials made available by researchers should be utilised by tech companies. This will help to predict code words or phrases used by terror groups in channelling algorithms of vulnerable individuals who may become potential recruits.
Overall, combating dangerous groups like the ISKP and al-Qaeda necessitates a smooth integration of cutting-edge technology, accurate intelligence, and international collaboration. It would be disastrous to ignore ISKP’s reach in cyberspace. The decision should be straight forward but with the best possible strategies to fight intelligently and innovatively.
Fahadh Firoz is a final year Masters student in the Department of Geopolitics and International Relations at Manipal Academy of Higher Education (MAHE), Manipal, India. Fahadh’s research focuses on terrorism, radicalization, and security dynamics, particularly in the Middle East and South Asia. Fahadh recently presented his research paper titled “The Rise of ISKP: Analyzing Multilingual Radicalization, Regional Alliances, and Global Threats” at the 10th Istanbul Security Conference, with its forthcoming publication.
Linkedin.
