Introduction
Kiwifarms was an internet forum known for its active targeting and harassment of trans people. In August 2022, the forum set its sights on Canadian Twitch Streamer and trans activist, Clara Sorrenti, also known as Keffals. The forum members called in the police to a fake bomb threat to her home and subsequently tracked her around the world once she fled Canada. If this harassment had occurred on a major social media platform, Sorrenti may have had some recourse to a form of content moderation. However, as Kiwifarms is a standalone website with no content moderation infrastructure or Trust and Safety teams, she had no such recourse. Instead, Sorrenti utilised her online following, starting a ‘Drop Kiwifarms’ movement to get the site kicked off the internet by targeting the companies that allow them to operate. The primary target of this campaign was Cloudflare, the content delivery network (CDN) providing services to Kiwifarms. Cloudflare stopped offering services to Kiwifarms in September 2022.
While considerable attention has been paid by researchers to the effectiveness of content moderation on social media platforms, and messaging applications, less attention has been paid to if and how infrastructure and service providers including CDNs deal with terrorist and violent extremist content (TVEC). CDNs play an important role in deplatforming websites by refusing to provide service. Denial of service by CDNs has resulted in the takedown of a wide range of websites such as The Daily Stormer, 8chan, and a variety of Taliban-owned websites.
This Insight provides an overview of what CDNs are, what content they host, and their role in countering TVEC online. While CDNs are a necessity in the modern internet ecosystem for websites to operate, there is no consistency in CDNs’ approach to addressing TVEC being hosted on their servers. The lack of a clear standardised process of content moderation may lead to the current situation where CDNs ignore or remain ignorant of the prohibited use of their services without sufficient public pressure.
How do CDNs work?
A content delivery network, or content distribution network (CDN), is a geographically-distributed network of proxy servers and their data centres. The goal is to provide websites with high availability and performance by distributing the service spatially relative to end users. CDNs came into existence in the late 1990s as a means to alleviate the performance bottlenecks of the Internet as it was starting to become a mission-critical medium for people and enterprises.
Joan Donovan places CDNs on Level 4 of the ‘tech stack’ (Fig.1) – a way of explaining how the internet functions. On Level 4 of the stack, CDNs help match user requests with local servers in order to reduce network strain and speed up websites. Without them, popular websites would, with enough traffic, be slowed to the point of unusability or forced offline due to server overload. The key question for this Insight is whether a CDN should be considered a host or simply a cache for this data. For internet service providers, they act as a means of distributing demand between servers, however, for website owners, they can be seen to act as a ‘surrogate host’. The implications of this will be explored below.
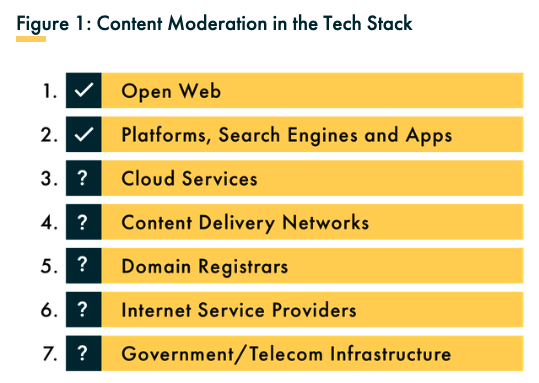
Fig. 1: Joan Donovan’s conception of the ‘tech stack’
CDNs are also essential for dealing with malicious access attempts, specifically denial-of-service attacks (DoS) that aim to overwhelm a server. These act along the same logic as server overload due to popularity. One way to facilitate such an attack is to trick the server into forming an increasingly long queue of users it is trying to communicate with. A distributed denial-of-service (DDoS) attack is the same process but utilising a network of computers. This can either be a peer-to-peer network of users attacking the same target or a ‘bot net’ of hacked computers. The advantage of the distributed approach is that while a server could simply block the IP address of a single attacker, it is much more difficult to block a distributed network with multiple redundant IP addresses.
CDNs and Extremist Websites
Tech Against Terrorism’s report into terrorist and violent extremist-operated websites shows the importance of examining websites and their surrounding infrastructure. It identifies 198 websites assessed as being operated by terrorist actors or by violent extremists that pose a credible and urgent threat to society. 79 of these sites related to violent Sunni Islamist actors, 18 to violent Shia Islamist actors, and 101 linked to the violent far-right. The report examined a representative sample of 33 websites, finding that 91% displayed audio/visual propaganda, 73% had an archive of historic content and 57% contained a communication feature. The total average monthly visits to these 33 sites was 1.54 million.
This Insight stems from a forthcoming article in Policy & Internet examining 56 extremist websites and their CDN providers. In line with Conway and Looney, the examined websites were divided into categories based on the believed operators of the site. The first is Terrorist Operated Websites (TOW) – sites that are expressly and officially affiliated with a terrorist group or movement. The second category is Ideologically Adjacent or ‘Fellow Traveler’ websites (IFT) which, although unaffiliated with particular terrorist groups, are ideologically supportive of such groups or movements and are thus extremist in their orientation. The third category examined here is Conspiracy Sites. These sites were drawn from Hanley et al’s study of QAnon believers’ website consumption and accordingly are largely focused on QAnon. However, other conspiracy theories such as those concerning COVID-19 and vaccinations were also found on these websites.
| Cloudflare | Nginx | Apache | Litespeed | Squarespace | |
| Terrorist Operated Website | 2 | 3 | 2 | 1 | 0 |
| Ideological Fellow Traveler | 13 | 5 | 2 | 0 | 0 |
| Conspiracy Sites | 8 | 15 | 4 | 0 | 1 |
| Total | 23 | 23 | 8 | 1 | 1 |
Table 1. Websites per CDN Provider
Cloudflare and Nginx are the main providers of CDNs for the websites present in the sample, providing services to 46 of the 56 websites. The eight terrorist-operated websites present in the sample are evenly split between Cloudflare, Nginx, Apache and Litespeed, with only Squarespace lacking a TOW. It is important to note that the TOWs present here are ideologically diverse, including websites affiliated with Hamas, Kurdistan Workers’ Party (PKK), Al Qaeda, the Popular Front for the Liberation of Palestine (PFLP), Earth First!, Blood and Honour and Hizbullah. This is not an issue relegated to any one particular extremist group or movement.
In terms of IFTs, Cloudflare supports the most (13), compared to Nginx’s 5 and Apache’s 2. Ideologically, these IFTs are split between violent jihadist and extreme far-right websites representing groups and movements such as the Nordic Resistance Movement, Patriot Front, the American Nazi Party, Identity Evropa, Blood and Soil and the Daily Stormer. The violent jihadist IFTs were supportive but not expressly affiliated with groups such as the Muslim Brotherhood, Hizb ut-Tahrir, and Jaish ul-Adl. The largest category in this dataset was the Conspiracy Sites, with the majority being provided with a CDN by Nginx (15/28) and Cloudflare (8/28).
Each of the examined websites was then classified according to Davies et al’s web extremism and recruitment scales. It should be noted that this coding was conducted solely by the author which may limit the reliability of results. The web extremism scale ranges from Level 1 to Level 4. Level 1 websites are informational only and the information presented actively avoids the presentation of violence or the use of hate speech. A Level 2 website also avoids the presentation of violence but encourages visitors to join the site’s cause in some manner. Level 3 features violent content without explicitly encouraging participation in the website’s cause. Level 4 actively encourages individuals to support the cause, including through violent actions.
Following this, the recruitment framework orders websites from 0 – 3. A website with a 0 rank contains no recruitment materials at all. A website with a 1 rank points towards the presence of efforts to pique the curiosity of site users, such as public discussion forums or opportunities to subscribe to newsletters and magazines. A 2 rank refers to the encouragement of ‘indirect action,’ such as donating to the group or cause or maintaining of the website itself. Finally, a score of 3 indicates active recruitment, including announcements and invitations to events as well as overt calls to ‘real world’ violent action.
| 1 (Fact Based) | 2 (Join the Cause) | 3 (Displays of Violence) | 4 (Calls-to-Violence) | |
| TOW | 4 | 2 | 1 | 0 |
| IFT | 3 | 7 | 10 | 0 |
| CS | 19 | 6 | 3 | 0 |
| Total | 26 | 15 | 14 | 0 |
Table 2. Extremism Scale per Website Type
| 0 (None) | 1(Passive) | 2(Indirect Action) | 3 (Active) | |
| TOW | 5 | 0 | 1 | 2 |
| IFT | 5 | 4 | 5 | 5 |
| CS | 2 | 6 | 20 | 0 |
| Total | 12 | 10 | 26 | 7 |
Table 3. Recruitment Scale per Website Type
None of the examined sites meet the requirements for Level 4 on the extremism scale, as none actively incite users to take violent action for the cause. The largest category (26/56) of websites scored a 1 but this is largely due to the presence of the conspiracy sites which, for the most part, avoid calls to violence, action or hate speech. Rather, they are focused on spreading misinformation in accordance with their chosen conspiracy, predominantly QAnon.
The IFT sites skewed more towards 3, as they feature violent imagery and hate speech but stop short of direct calls to violent action. Finally, the TOW sites were mostly focused on providing information to the user about the groups’ efforts. In terms of recruitment, the websites were mostly focused on soliciting funding to maintain the group or website (26/56), rather than actively encouraging participation in group activities (7/56). There are a wide variety of groups and TVEC content present on these websites, and hence an urgent need for regulatory clarity on the role CDNs play in moderating TVEC.
Existing Legislative Pressure on CDNs
It’s clear that CDNs are essential for extremist-affiliated websites to operate, however, it is not clear what legislative pressure there is on these companies to moderate the websites to whom they provide services. As stated above, the key question is whether a CDN should be considered a ‘surrogate host’. Article 3(g) of the Digital Services Act (DSA) clarifies issues surrounding CDNs by defining intermediary services as three separate categories: ‘mere conduit’ services, ‘caching’ services and ‘hosting’ services. Each is subject to different liabilities and obligations, however, the latter two will be discussed here as they are most pertinent to CDNs.
Hosting service providers are more liable for the content they host than ‘caching’ service providers are liable for the content they temporarily cache. In each, the liability is subject to a number of conditions, however, the important thing for CDNs in terms of content moderation is that they are seen to be a ‘caching’ service.
This is important in this context, as it isn’t clear whether a CDN such as Cloudflare or Nginx should be considered a ‘caching’ service or a ‘hosting’ service. CDNs are left in an awkward position in that their different functions may or may not leave them liable for particular obligations. Considering that the surrogate hosting function concerns terrorist and extremist content, it remains to be clarified whether CDNs can rely on being treated as caching services rather than hosting services. Without this clarification, content moderation by CDNs will continue to be done in a haphazard manner lacking in legal certainty.
Conclusion
Content Delivery Networks (CDN) are necessary for websites to operate in the modern Internet ecosystem. Without them, websites are liable to be either too slow to function or overloaded with user requests, legitimate or otherwise. It does not appear that there is any consistency in CDNs’ approach to TVEC being temporarily hosted on their servers and whose services allow them to operate. The lack of a clear standardised process of content moderation may lead to the current situation where CDNs ignore or remain ignorant of the prohibited use of their services until public pressure and the negative press become insurmountable.
Seán Looney is a Lecturer in Criminology at the University of Plymouth. His research interests include the regulation of online terrorist and violent extremist content and the impact of bulk surveillance on the promotion and protection of human rights. Sean undertook his PhD at Swansea University as a member of CYTREC. He is a member of the VOX-Pol research network and is a former member of the GIFCT Positive Interventions and Strategic Communications Working Group and the GIFCT Legal Frameworks Working Group.
Twitter: @_Sean_Looney_
