The Turkestan Islamic Party (TIP) is considered the most prominent Salafi-jihadist terrorist organisation that originates from China. While it aims to establish an Islamic Emirate in Xinjiang, it has been active primarily in Afghanistan and Syria. Activities, ideology, and ambiguous organisational structure of the TIP have been subject to heated academic debate in recent years. However, scientists have attached little to no attention to understanding its online propaganda activities, which contrasts with the popularity of studying Islamic State’s or al-Qaeda’s presence in cyberspace.
This note selectively summarises findings of the investigation of the information ecosystem maintained by Islam Awazi (IA) – a propaganda bureau of the TIP – that was carried out in September 2020. It aimed to map online communication channels exploited by the group and learn its capabilities in producing new releases and attracting an online audience. Detailed results of this research project were included in a paper published recently by Studies in Conflict & Terrorism.
Methodology
This project was primarily founded on open-source intelligence (OSINT). A number of OSINT techniques and tools, including advanced options of surface and deep web search engines, Recon-NG and Metagoofil scripts in Python, as well as SpiderFoot online reconnaissance app, were utilised. There were three phases of the investigation. The first consisted of actions aiming to discover web pages and social media profiles belonging to the TIP/IA. The second extracted as much data from the identified communication channels as possible, including usernames, e-mail addresses, external and internal links, or IP addresses. The third used newly collected data to detect other interconnected means of online propaganda dissemination.
Subsequently, a limited content analysis was utilised to measure the monthly propaganda output of Islam Awazi in 2020. Its structure was also examined. All detected productions were coded as audiovisuals, visuals, audio, text pieces. Finally, a sample of 112 videos from the IA’s homepage, released between February 2019 and September 2020, was analysed to grasp the correlation between their thematic composition (tags) and viewership.
Islam Awazi’s Presence and Activities on the Web
The OSINT investigation discovered a network of communication channels composed of three standalone websites, six Telegram channels, 44 file-sharing services (including the Internet Archive), two Flickr accounts, and a Soundcloud profile. Additionally, a niche Videoara service was utilised by the group.
This ecosystem proved to be concentrated around one standalone website – Muhsinlar #1 – which constituted the leading aggregator of the TIP-affiliated propaganda on the surface web. It was connected through external links with two other inactive domains – Muhsinlar #2 and Islamawazi. Aside from them, Muhsinlar #1 also promoted three official channels of the TIP/IA on Telegram. Other detected channels shared similar content with the previous three. In addition, one of them advertised the Muhsinlar #2 website. All of them consisted of between 316 to 1422 members as of September 2020.
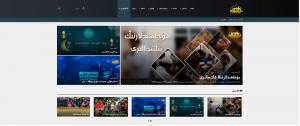
Figure 1. Screen capture of the Muhsinlar #1 website
Two other standalone websites, while inactive, provided fascinating findings. Analysis of their IP addresses allowed to discover – through reverse IP lookup – that they were hosted on the same server that also maintained hundreds of other web pages containing either pornography or malware. Muhsinlar #2 was co-hosted with 199 other domains, and at least 20 of them were labelled as malicious. Attempts of accessing them through a Linux-based virtual machine triggered malware warnings. Islamawazi was co-hosted with 129 other domains, and at least 93 of them contained malicious software, according to the SpiderFoot database. Two explanations of this situation can be offered. On the one hand, these findings suggest that the TIP/IA could merely rent hosting on servers accidentally owned or used by the cyber-criminal underground. On the other, it is also possible that the group was somehow involved financially or organisationally in maintaining these domains. Unfortunately, not enough evidence was collected to support either of these explanations.
The two profiles of the TIP on Flickr were created in 2014 and 2017. They shared a limited number of advertisement banners and pictures of mujahidin. They attracted little attention from an online audience and seemed abandoned as of 2020. Likewise, the Soundcloud profile that shared several anasheed was accessible but inactive. Few old pieces of the TIP’s propaganda were also discovered at the aforementioned Videoara web page.

Figure 2. One of the advertisement banners published by the IA on Flickr
Finally, the investigation discovered multiple accounts affiliated with the Turkestan Islamic Party and its media bureau on Internet Archive. Each profile usually published a few pieces of propaganda before it went inactive. Overall, at least 300 productions of the group were identified. Available data suggests that the first releases of this VEO were published on this platform in 2010. Interestingly, some profiles did not disseminate propaganda but served as beacons redirecting users to external services. Links leading to at least 43 file-sharing websites, such as megashare.com, megaupload.com. rapidshare.com, uploadstation.com, or 2share.com, were discovered.

Figure 3. Screen capture from the “martyrdom operation” video that IA published on Internet Archive in March 2020
Measuring the Output and Impact of IA’s Online Propaganda
Content analysis of the discovered environments proved that Soundcloud and Flickr constituted purely secondary channels of propaganda dissemination of the group. The first consisted of only three anasheed that were viewed by several hundred Internet users each. The two Flickr accounts published 30 images combined and were visited more than 5,500 times as of September 2020. Videoara consisted of only four productions of the TIP.
In contrast, the Internet Archive constituted a significant propaganda distribution channel of the Turkestan Islamic Party. OSINT investigation detected at least 336 positions affiliated with this organisation, including 130 audio files, 61 text files, 29 images, 114 videos, and two Android applications. Some of them attracted noticeable attention from the online audience. For instance, the two most popular e-books of the TIP were visited more than 47,000 times. It is, however, quite probable that the viewership of these releases was heavily influenced by the fact that they were accessible on Internet Archive for years.
The Muhsinlar #1 served as the primary aggregator of the TIP/IA’s content in 2020. It consisted of several sections: Movies, Invitations, Weekly News, Khurasan, Radio, Books and Newspaper. They contained hundreds of audio and video productions, including 200 audiovisuals in the Movies section and 333 weekly audio recordings. The web page also distributed 62 issues of Islam Awazi’s e-magazine. Audiovisual propaganda productions of the group usually focused on traditional Salafi-jihadist narratives, including religious indoctrination, martyrdom, battle footage from the frontlines of Syria, as well as pieces that depicted the process of brainwashing children. Interestingly, these materials that provided news to the followers frequently re-used propaganda productions released by other violent extremist organisations, such as Hayat Tahrir al-Sham. Nevertheless, the quality of these productions was rather mediocre.
Quantitative analysis of the content of Muhsinlar #1 allowed to discover that Islam Awazi’s output was considerable when compared to other Salafi-jihadist organisations. Between January and September 2020, IA released, on average, four radio broadcasts, four weekly reports, and more than eight videos monthly. Interestingly, this media office attached little importance to releasing new text releases. In nine months, it published only six e-books and one issue of its flagship magazine. Overall, IA released 164 new propaganda pieces on its website between January and September 2020.
Their popularity was mediocre at best. Analysis of the sample of 112 videos proves that, on average, each piece was viewed only 134,7 times. Nearly 50% of the sample was visited less than 50 times. As of September 2020, there were only 17 videos that were viewed more than 200 times. Three of them were instructions that focused on the use of firearms, while the rest consisted of less dynamic formats, such as religious lectures.

Figure 4. Screen capture of the IA’s instructional video published at Muhsinlar #1
Conclusion
These findings show that the propaganda bureau of the TIP has maintained a rather simplistic information ecosystem concentrated around one standalone website, serving as the main propaganda repository, which was supported by six Telegram channels. Other discovered URLs, while usually still accessible, were outdated and inactive. It effectively suggests that the online activities of Islam Awazi have not been actively curbed by law enforcement and Internet companies for years. Overall, the identified information ecosystem maintained by TIP/IA contrasts with those exploited by more prominent Salafi-jihadist violent extremist organisations that are usually much more sophisticated in promoting their agenda in cyberspace.
The TIP stands out, however, in terms of unexpectedly high propaganda output. Still, its productions have attracted relatively little attention from the online audience. This may have been caused by the fact that almost all of them were released in Uyghur exclusively.
Finally, it should also be emphasised that the TIP utilised the Internet infrastructure, which was somehow involved in a cyber-criminal activity. While the true nature of this connection remains unclear, it may constitute a sign of the existing and widely debated terror-crime nexus.
Miron Lakomy is an Associate Professor at the Institute of Political Sciences, the University of Silesia, Poland. He was a visiting fellow at the University of Oxford and the European University Institute and a visiting scholar at the University of Cambridge. His research focuses mostly on online terrorist propaganda and he has published in world-leading journals in the field of security studies, including Terrorism & Political Violence, Studies in Conflict & Terrorism, and Security Journal.
