Operational security (OPSEC), both online and offline, remains a priority for many violent extremist groups and their members. As such actors’ adoption of communications technology has increased, so have the risks of using digital forms of engagement, security-related and otherwise. While extremists conventionally emphasise the importance of taking steps to evade detection, avoid disruption, and continue their efforts to promote their worldviews, some movements and individuals are more vigilant than others. Over the last week alone, in the aftermath of the 6 January attacks on the US Capitol, some actors associated with and sympathetic to the attacks have worked to address vulnerabilities with countermeasures. These measures were likely motivated by the identification and arrest of persons documented inside the Capitol building, some of whom face repercussions outside the legal system, too. The shuttering of various social media platforms, channels, and users has also fueled this trend. On Telegram, a few OPSEC minded channels have increased efforts to support sympathisers needing guidance about how to operate securely. Ultimately, such developments may have implications for security personnel’s efforts to identify perpetrators in the future.
Although far-right extremists and conspiracy theorists are unoriginal in their endeavors to offer like-minded peers instructions on operating safely online, past research featured on GNET, along with the following article, showcases increasing commitment to operational security from the far-right. Oftentimes, that guidance addresses what communication platforms extremists should use, which represents an ongoing challenge, but today, other notable patterns are emerging, too. To better understand this phenomenon and discuss the problem, the following Insight examines two digital OPSEC trends that have been increasingly prominent on online forums, namely Telegram, since the Capitol’s 6 January attacks. The first half looks at guidance concerning “cross-domain OPSEC” among far-right extremists and conspiracy theorist networks online, and the second half explores the exposure of wider audiences to the value of rudimentary OPSEC precautions.
Cross-Domain OPSEC
First, in this article, “cross-domain OPSEC” refers to the specific countermeasures individuals and groups may take to avoid connections between their offline activities and online presence. In the wake of the attack, information-sharing practices consistent with cross-domain OPSEC is prevalent among some groups. This uptick is likely because failures to follow such principles meant that negligent practices online further compromised individuals participating in the Capitol attack in person. According to news reports, some people involved in the Capitol’s breach tried to remove incriminating material from online profiles and delete their social media accounts but lacked control over the range of evidence documenting their actions.
Thus, although extremists’ interest in OPSEC is not new, the attack on the Capitol by far-right extremists was relatively unique because it happened in broad daylight with hundreds of news crews and the participants themselves filming and archiving the day’s events. Recognising the investigative value of such information, the Federal Bureau of Investigation put out a call for information from numerous sources, receiving more than 100,000 pieces of digital content in the days after the attack. Combined with crackdowns on various social media platforms, these dynamics increased concerns about digital and physical OPSEC in isolation, but also in the form of cross-domain OPSEC, which may offer bad actors lessons for the future.
Within 24 hours of the attack, one online channel posted a link to a news story that noted that the “FBI’s digital media team is currently hunting down U.S. Capitol protestors on social media websites. Acting AG Rosen says some participants ‘will be charged today’ and more arrests to come.” Users disseminated the post across several different channels. This prompted a separate channel’s administrator(s) to lament the accompanying failure to properly observe cross-domain OPSEC by saying, “From an OPSEC perspective, we all witnessed many clear mistakes by those who roamed the halls of the Capitol building” before offering specific tips for obscuring one’s physical identity. Although these points clearly relate to physical OPSEC, the cross-domain nature is clearly at the forefront of the conversation because of the considerable number of identifiable images and information available on social media.
The same channel underscored the importance of cross-domain OPSEC in a later post, noting that:
The enemy is actively watching Telegram and cataloging what is said, by whom, and the time they said it. From this they can guess about your timezone. This information alone can be dangerous if they only need to confirm their suspicions. So remember, be VERY careful about what you post. Pictures of pets, tattoos, surroundings, etc… can all assist the enemy in discovering your identity. So remember, once data is out there it never goes away.
This guidance, made in an online forum, is designed to help individuals evade detection and identification through the combination of online activities and offline connections. Beyond potentially compromising information from social media, another area concerning cross-domain OPSEC concerns cell phone data. On 9 January, US Senator Mark Warner (D-VA) issued a statement about his efforts to urge wireless carriers including AT&T, T-Mobile, and Verizon, along with a suite of technology companies, to preserve evidence related to the attack on the Capitol. Meanwhile, on Telegram, channels and users supportive of the attack offered guidance about updating phone setting to mask their location and provided directives like “Do not take your personal cell phone with you to an event of this nature. Leave it at home.” While concerning cross-domain OPSEC, this anecdote touches on the next notable trend among this base of users: a renewed emphasis on protecting one’s privacy.
Re-Emphasising Basic Privacy Settings
Basic digital OPSEC is not new or necessarily an indication of illicit or clandestine behaviour. In fact, many basic techniques to protect one’s identity are recommended by a range of institutions, from technology companies to civil rights organisations. Despite such recommendations, most people tend to ignore or underperform when it comes to OPSEC principles.
However, it is also important to recognise that, as more public forums such as Twitter and Facebook become less hospitable to individuals or as other alternatives like Parler are taken offline, some individuals will likely migrate to platforms where OPSEC is a greater priority and more regularly practiced. Evidence suggests this dynamic is already occurring. The US Capitol attacks seem to have triggered a small online migration, with notable numbers of individuals moving from more public to more private platforms. Telegram announced, for example, that its user base increased by around 25 million users over a 72-hour period from 9-12 January.
A segment of those new users, particularly those joining networks affiliated with neo-Nazis, the Proud Boys, and other extremist movements, were greeted by calls for increased operational security. Even though the techniques highlighted in these recommendations were not necessarily new or reliably good guidance, they became a central part of the dialogue on many of these forums. Thus, even if new users had not practiced digital OPSEC in the past, or sought information about countermeasures, it became commonplace across these platforms after 6 January.
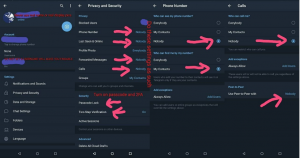
This screenshot, which made the rounds on a number of different channels, is just one example of the advice given to Telegram users, demonstrating how to reduce the amount of information other users can access. Broadcasting recommendations to a similar audience, another channel posted a “Weekly reminder” of OPSEC principles similar to those depicted above, noting that practice of these tactics would “Keep, Journos, ‘Security Researchers,’ Commies, Antifa, and others from doxxing you.” It was then followed by tips regarding general privacy settings, including a “Bonus Item” to use an untraceable number to sign up for Telegram.
Though most of the recommended countermeasures appear to be relatively rudimentary (and occasionally counterproductive), further mainstreaming an emphasis on OPSEC, and making guidance more accessible, may lead more people to adopt such practices in the short- and possibly long-term. The effects of this push for increased informational and operational security are something that requires more research and analysis in the future.
Conclusion
The use of digital tools by extremists will persist, continually adapting to the interventions made by governments or private technology companies. This trend is already demonstrated by this demographics’ exploitation of numerous platforms, but at least anecdotally, these trends OPSEC guidance recommendations for extremists supportive of the attack on the Capitol can go well beyond tools. It is critical to recognise that some events and interventions might jumpstart the OPSEC practices of extremists, energising some users’ desires to enhance their security to avoid detection by law enforcement, disruptions by service providers, and monitoring by journalists and researchers alike. Though this trend is concerning, relevant stakeholders must also understand that more advanced OPSEC skills take time and effort to develop and maintain. Although the proliferation of operational security skills among extremist communities is likely to increase, researchers and analysts can and should continue to monitor this activity, and private companies and law enforcement and intelligence practitioners must continue to adapt to this landscape as it evolves.
